-min.webp)
For years, building an effective, in-house SOC function felt like an organizational impossibility. The sheer resource drain required for a full Threat Detection, Investigation, and Response (TDIR) mandate forced many organizations to rely on external providers.
Today, however, a new wave of technology is fundamentally shifting the economics and operational feasibility of the SOC. The advent of AI SOC Agents (also known as AI SOC Analysts) pushes into an era where modern, high-performing SOCs can finally be built internally. However, we need to tweak how we think about our teams and processes.
A SOC focused on TDIR typically organizes its work around four critical functions:
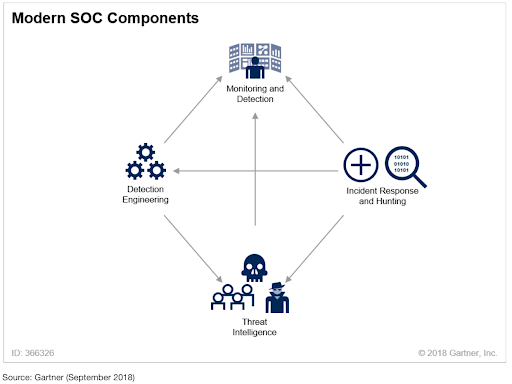
Before AI, these four functions required immense human capital. As a result, most organizations ended up outsourcing parts of the model to service providers, such as MDR providers.
While rational, this reliance on external providers brought its own set of problems. Many providers pursued economies of scale over quality, leading to service deterioration. Just like traditional MSSPs, many MDR providers became accommodated in relying on detection tools’ content to generate the necessary alerts, performing cursory, superficial triage and leaving critical context and deep analysis on the table.
{{ebook-cta}}
Some organizations attempted to solve the efficiency gap by adopting SOAR solutions. However, SOAR proved to be a difficult technology to deploy and maintain. Writing and maintaining playbooks became an herculean task, challenged by numerous variations, difficulties in integrating multiple tools and data sources, and the lack of a basic structural framework for the automated processes to fit in.
The AI SOC platforms are now bringing fresh air into the security operations center, enabling organizations to build truly modern SOCs. Functionally, the SOC still needs those four core functions, but the distribution of labor is changing dramatically.
AI SOC analysts can now effectively and efficiently automate the processes around monitoring, triaging, and investigating alerts. This shift allows human analysts to focus on activities where their unique expertise, judgment, and context are indispensable:
This new focus is supported by other modern developments. The evolution of common languages and frameworks, such as SIGMA and the MITRE ATT&CK framework, has streamlined detection engineering processes, making it far easier to assess threat coverage and quickly turn threat intelligence into detection content. Furthermore, exposure management solutions are providing great visibility around exposure gaps, enabling organizations to quickly address vulnerabilities before they are exploited.
The SOC of the future is similar to SOCs that have been built in the past few years, at least from a functional point of view. However, a new toolset has enabled a new distribution of human talent across those functions, making human resources far more efficient and reducing the attrition caused by toil and repetitive, manual work.
This technological evolution also changes the methodology for standing up a new SOC.
The old wisdom was to recommend a "create the process first, automate after" approach. This was necessary because SOAR required a defined, documented process to write into a playbook. But putting together a process in fully manual mode requires a lot of people and effort, so many organizations would get stuck in this phase. With AI SOC, this is no longer a prerequisite.
Modern SOCs today can be quickly built to start operating with a basic detection stack, some exposure visibility, and AI-SOC automation. But it doesn't stop her. This is not simply about throwing tools together.
The secret is enabling the team to quickly iterate. This means continuously using the output from AI-driven investigations and exposure scans to adapt and tune detection coverage, while providing crucial context to the AI-SOC analyst to improve its accuracy and increase the rate of fully automated investigations.
Similar to agile methodologies, the path is to quickly put together the technology framework, and continuously evolve from that starting point.
The journey begins more or less the same way, with good people in place (though with a leaner "first tier" team, which is no longer required). But instead of getting into neverending discussions about how the processes should look like, it moves to getting the tools in place immediately after. With the basic technology pipelines and feedback cycles in place, the processes are created and adapted quickly according to the organization's needs and special characteristics.
The continuous improvement and iterative nature takes over to further evolve not only the processes, but also the toolset and, ultimately, the team. The modern SOC is one that is built to learn, adapt, and scale—all thanks to AI empowering, rather than replacing, the human analyst.
Learn about Gartner's guidance on improving SOC capacity with AI agents