
-min.webp)
For many large organizations, the greatest security risks often hide in the periphery. While core production environments are strictly monitored, subsidiary infrastructure or legacy development environments can sometimes slip through the cracks of visibility.
We recently helped a customer uncover a textbook example of this "shadow risk": A true positive attacker scenario involving a dormant access key that hadn't been rotated in years. Here is how the attack unfolded, how Prophet AI identified the threat, and how the organization turned a near-miss into a major security win.
The story began in a subsidiary’s AWS environment, a part of the infrastructure where visibility was historically lower.
A dormant IAM user, originally set up for development purposes, suddenly became active. This account held an access key that had been created long ago and left forgotten. According to the investigation, the key had not been used to perform actions in the recent past, effectively making it a "zombie" credential.
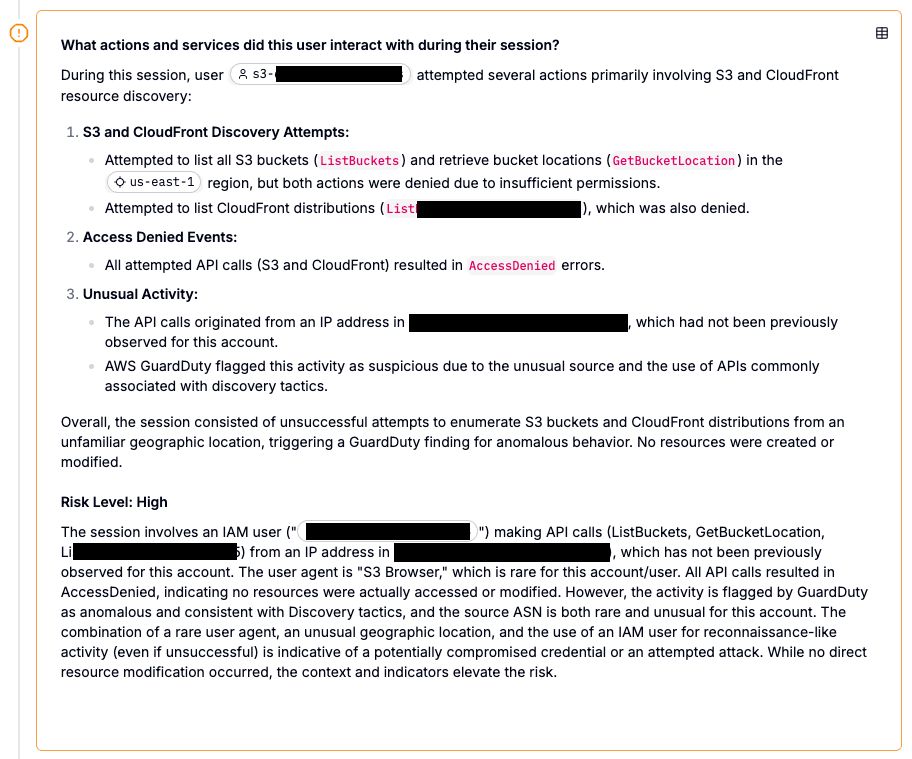
The quiet was broken when this identity began attempting to map out the cloud environment. The attacker executed a series of API calls typical of reconnaissance, specifically attempting to list S3 buckets (ListBuckets) and identify CloudFront distributions. Their goal was clear: discovery. They wanted to know what data existed and where it lived.
On the surface, the activity might have looked like a developer checking resources. However, Prophet AI’s investigation engine immediately flagged this behavior as highly suspicious by correlating multiple weak signals into a high-confidence alert.
1. Unusual Context: Prophet identified that the API calls originated from an IP address in a geographic location (Turkey) that had never been observed for this account before. Threat intelligence enrichment revealed the IP belonged to a VPN provider, often used by attackers to mask their true location.
2. Anomalous Tooling: Legitimate developers typically use standard command-line interfaces (CLI) or SDKs. Prophet detected that this session was using a third-party S3 browser tool, a "rare user agent" for this environment that signaled manual, non-standard exploration rather than automated system behavior.
3. The Behavioral Mismatch Perhaps the most damning evidence was the account history. Prophet analyzed the user's behavior profile and noted that this specific identity had never executed these discovery commands in the past 30 days. The sudden shift from "dormant" to "active reconnaissance" was a definitive indicator of compromise.
The result of the investigation already speaks itself, but could it be trusted? How did our customer know that everything that should be assessed in this case was checked by the agents?
Prophet AI includes all the information about the questions asked during the investigation, queries performed and data sources used. This case started with a single AWS GuardDuty alert, collected from a SIEM. As part of this investigation Prophet AI:
All the queries, as well as their results, are available to the user for review.
This level of thoroughness and transparency provides the assurance that SOC analysts need to trust the results of the investigations.
Fortunately, the principle of least privilege provided a safety net. The attacker’s attempts to list buckets and distributions resulted in AccessDenied errors. They knocked on the door, but it didn't open.
However, relying solely on permissions is a dangerous game. If the attacker had found a different, more permissive key, the outcome could have been data exfiltration.
Prophet AI’s alert allowed the customer to see the attempt clearly. Within minutes, the investigation confirmed:
The customer acted swiftly. The compromised access key, which hadn't been rotated in four years, was revoked.
Beyond resolving the immediate threat, this incident catalyzed a broader hygiene initiative. The customer used Prophet AI’s insights to audit their subsidiary infrastructure, identifying and removing other stale credentials that had accumulated over time.
This case serves as a great example of how AI in the SOC can help organizations apply a deep level of analysis to all signal sources, including those from less visible corners of the environment. By leveraging AI to automate the investigation of "low-fidelity" signals like failed API calls and unusual locations, security teams can shine a light on their darkest corners and catch attackers before they find an open door.
.jpg)
