
-min.webp)
"Living off the Land" has become a preferred tactic for threat actors in many attack scenarios. This time, existing, “benign” components are being used as part of phishing campaigns. By leveraging the reputation of trusted services like PayPal and Zoom, attackers can slip past traditional Secure Email Gateways (SEGs) that whitelist these domains.
Recently, Prophet AI investigated a phishing alert that turned out to be related to a highly sophisticated variation of this tactic: a Telephone-Oriented Attack Delivery (TOAD) campaign weaponizing Zoom’s own authentication infrastructure.
This investigation highlights not only the ingenuity of modern attackers but also the necessity of AI-driven analysis that looks beyond verified headers to understand the intent within.
The attack vector Prophet AI identified is elegant in its simplicity but dangerous in its execution. Unlike standard phishing emails that spoof a domain, this attack generates a legitimate email from Zoom itself.
Here is the mechanism the attackers employed:
The Result: The victim receives a forwarded email. Because the email originates from Zoom's official infrastructure, it passes standard authentication checks (SPF/DKIM). When the victim opens it, the Zoom template reads:"Hello Dear Customer, Your PayPal will be auto debited..."
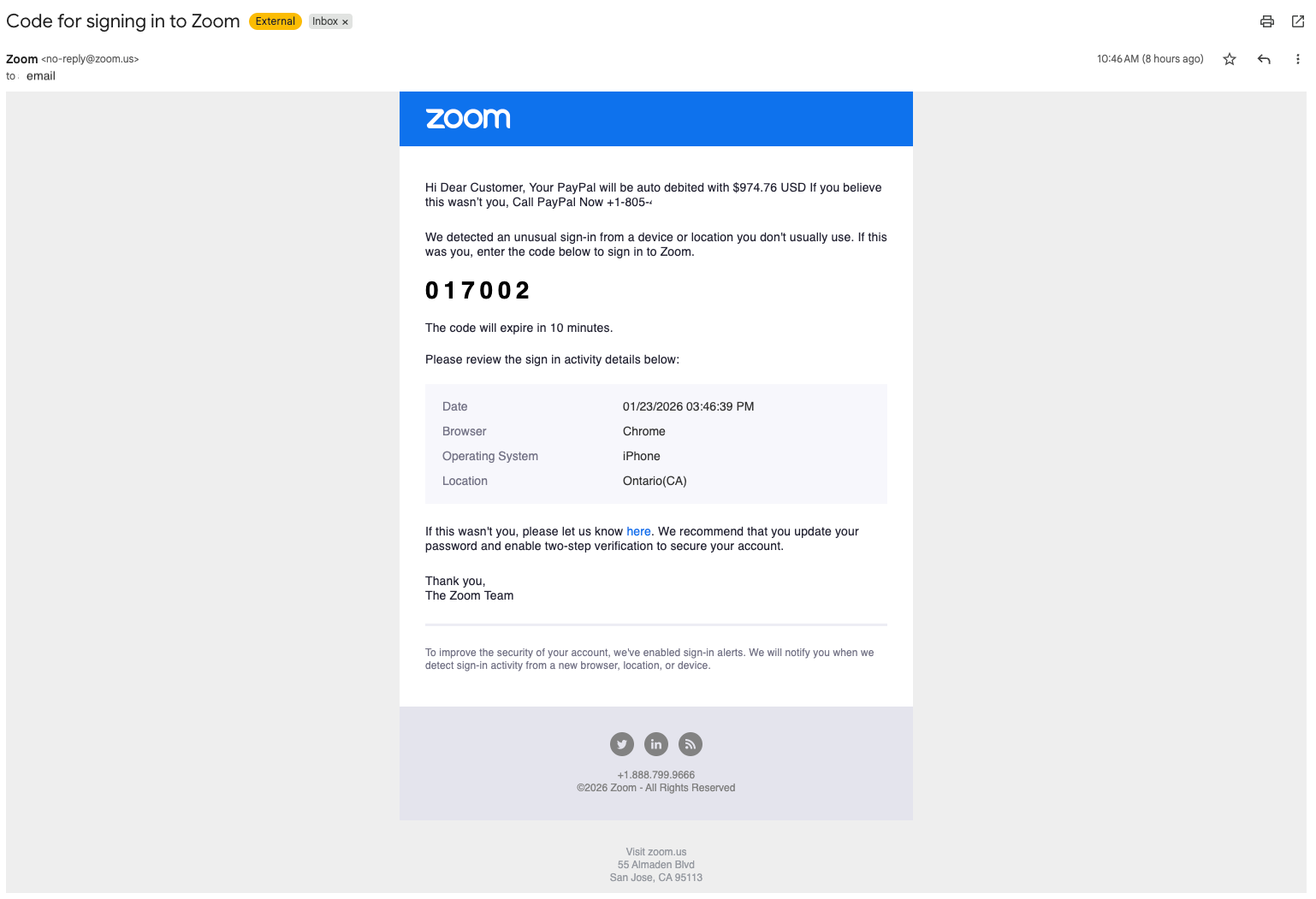
This technique creates a "verified" trojan horse. The email is technically safe—it contains no malicious links or malware—but the text itself is a social engineering trap designed to panic the user into calling the fraudulent support number.
While traditional filters might see a "Safe" email from zoom.us or a forwarded message with valid headers, Prophet AI analyzes the contextual intent of the content.
Upon processing the raw email, Prophet AI immediately flagged the message despite its legitimate origin.
Prophet AI ran 138 queries on 11 data sources for this case, all that in just 5 minutes!
This attack mirrors the obfuscation techniques seen in recent campaigns, where the payload is hidden in plain sight within the legitimate fields of a trusted service.
The specific danger here is the erosion of trust. Users are trained to look for legitimate senders. When they see an email that is genuinely from Zoom (or forwarded from a genuine source), their guard drops. The attackers rely on this "halo effect" to bypass scrutiny.
By identifying the discrepancy between the sender (Zoom) and the content (PayPal financial urgency), Prophet AI successfully identified the trap as a real attack before it could result in financial loss.
As attackers continue to exploit the features of the tools we use daily, the definition of a "malicious email" must evolve. It is no longer enough to verify who sent the email; we must verify what they are saying.
The required analysis for cases like this goes beyond what is usually part of the static playbooks used by Level 1 analysts. This is a typical case that can confuse a junior analyst, requiring an escalation to Level 2. While many AI SOC products focus on automating typical L1 alert triage, Prophet AI goes beyond that, saving time not only from typical L1 tasks but also reducing the overhead on the more expensive L2 and L3 resources.
With the additional complexity in attacks like this, reported phishing and email alerts require complex investigations that cannot be performed efficiently with a humans-only approach. Prophet AI adds machine-level scale and velocity, all that while performing thorough and complete analysis. Deploying Prophet AI for phishing is an easy way to improve investigations outcomes while keeping costs under control and reducing MTTR to a level compatible with the high speed threats of today.
Prophet Security responsibly reported the attack methods and use of Zoom resources to Zoom before publishing this analysis.
.jpg)
